Chapter 3: Linux Basic Command
Hello and welcome back to the course. today we discuss some Linux command that helps us to make our task easy. I make this course for beginners so if you already know how to use Linux you can skip this part.
Linux Terminal Command
In all the Linux based system you can do all the work from this powerful terminal.
pwd
pwdls
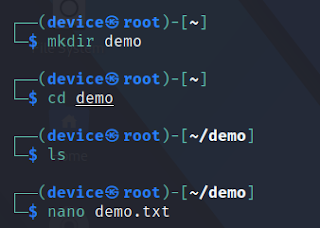
lsls -la # show all the informationls /path to show filesls /home # show home directory filesmkdir demo # make directory cd demo # change directory cd /path # you go diectly with currect path cd .. # for one step back to the file path nano demo.txt # make fileWrite as you wish and after you have to write with ctrl+o and enter.
cat
cat demo.txtmv
mv demo.txt /home/device/Download # move to Downloadmv demo.txt /home/device/jay.txt #rename chmod
chmod +x jay.txt--- --- ---o g e o= file owner g= group member
e= for all
r (read) = 4 w (write) = 2 x (execute) = 1 no permissions = 0# you can write as chmod 777 [file name] #give all the permissionchmod 600 #give permissionn to owner read and write else give nothingrm
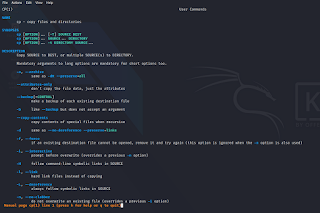
rm -r jay.txtYou can remove any file in on any pathrm -r [path]man
man cpTerimination
Thank you for coming to this site. If you Like this tutorial please share with your friend and family. I make an amazing tutorial in this blog. If you have any queries and question ask me in the comment section below.